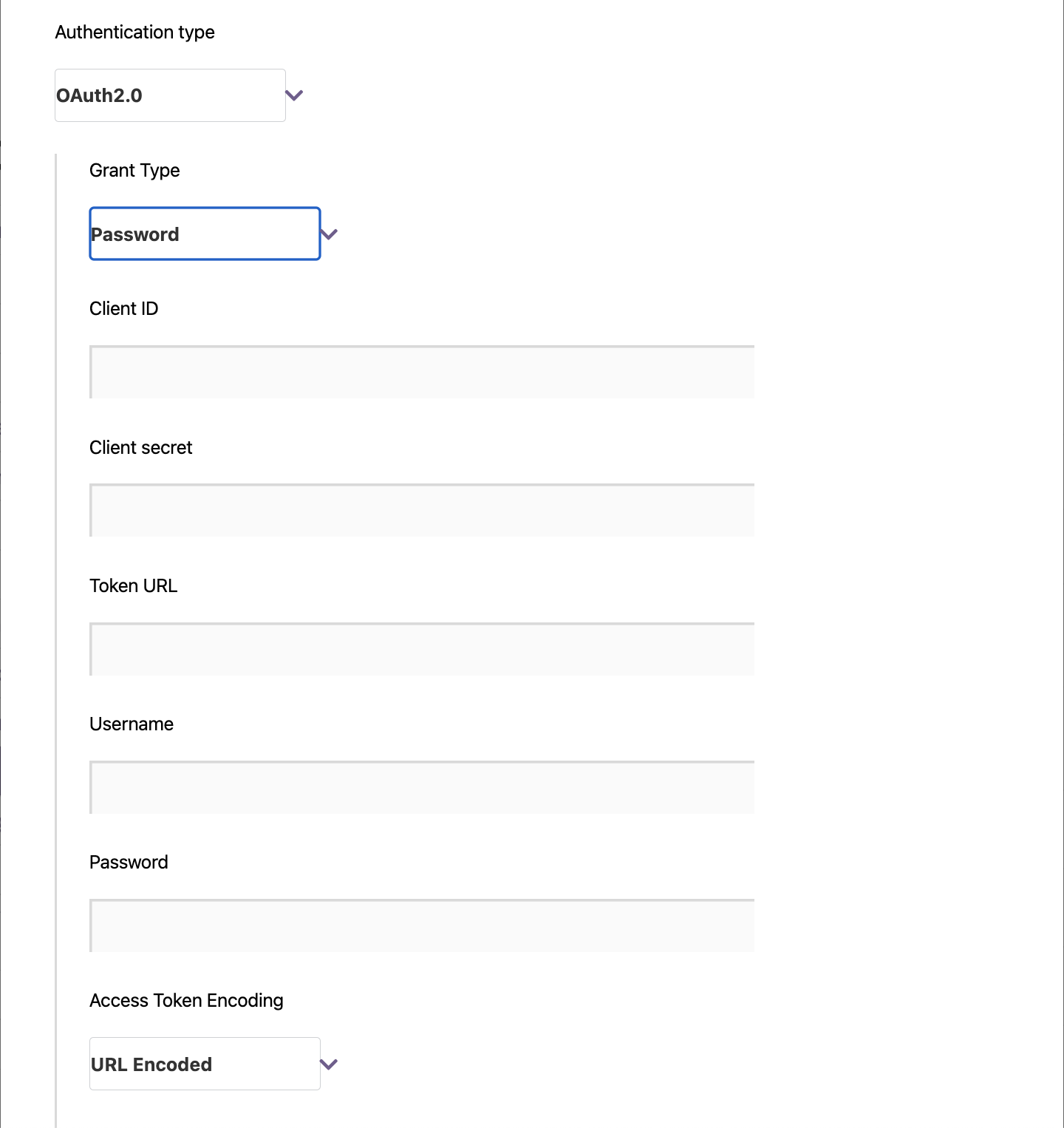
Vouched plug-in for Alloy SDK
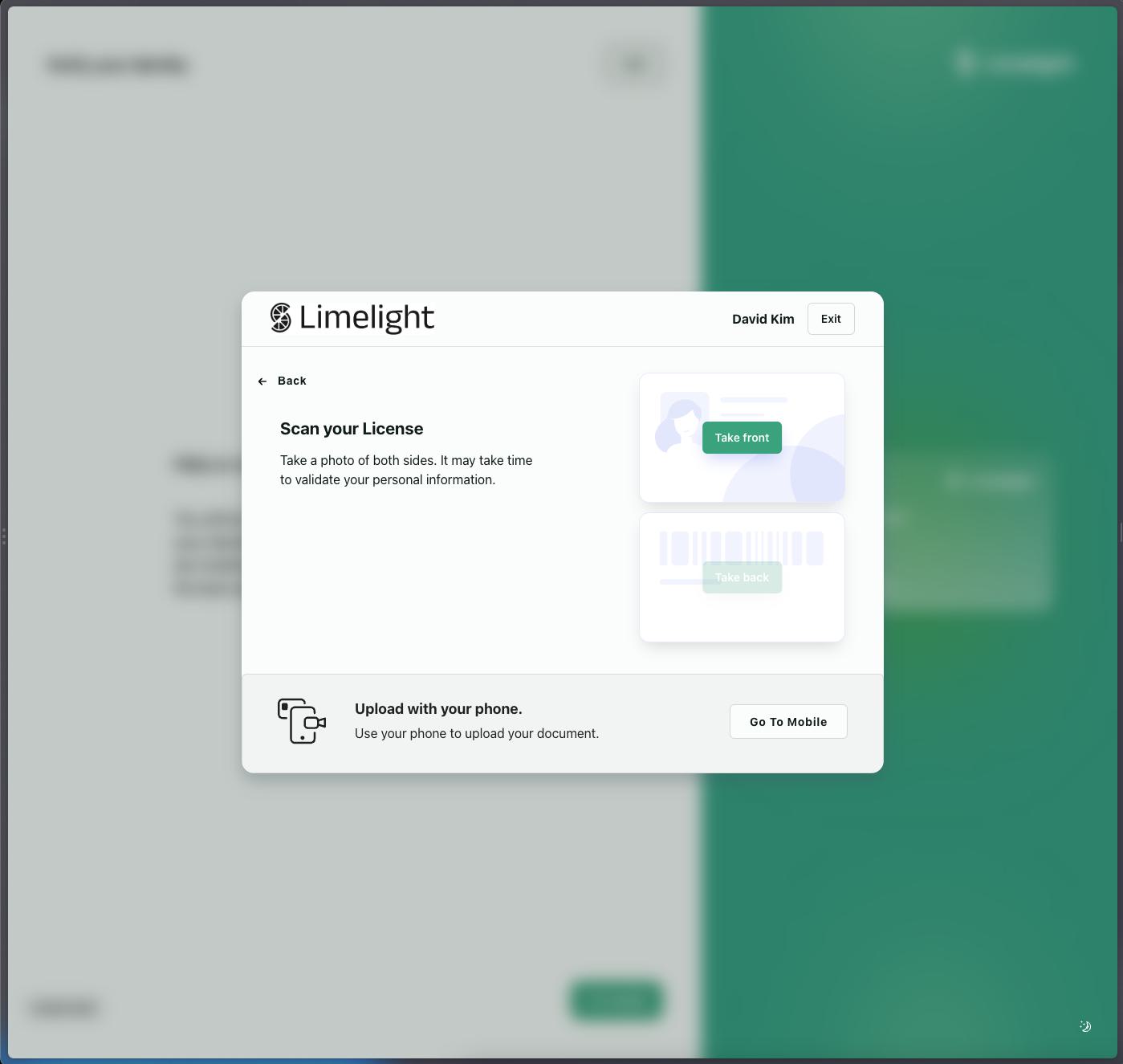
The Alloy SDK now supports the Vouched document verification flow. Vouched leverages proprietary artificial intelligence to fully verify identity and onboard users in seconds.
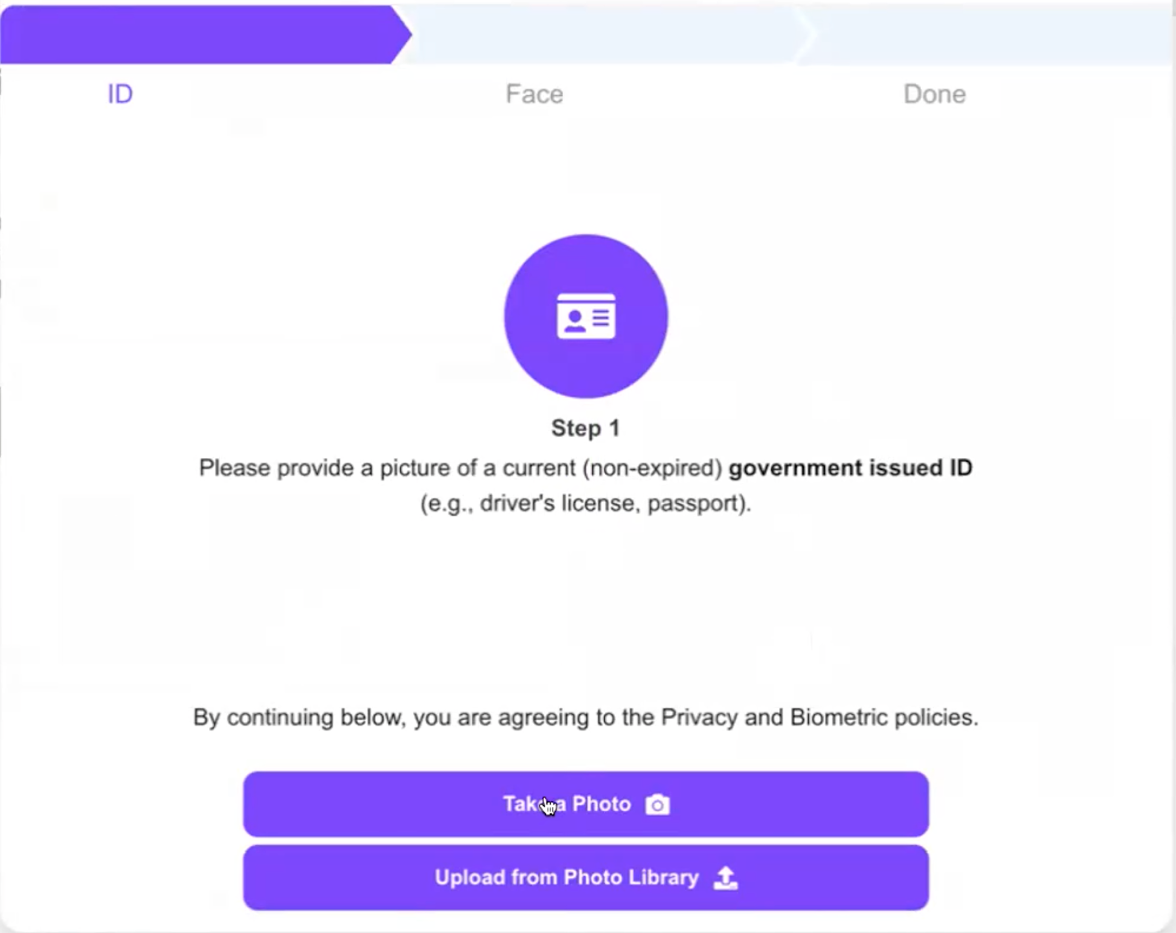
If you’re already using the Alloy SDK, simply select "Vouched" as a plugin option in your workflow.
No code changes are required. Dashboard setup instructions are here and API docs are here. Reach out to your CSM if you'd like to get it set up.