Share
Synthetic identities: why fraudsters need imaginary friends
Jun 6, 2024
Synthetic identity fraud is changing, but the mode of operation remains the same: mixing real and fake information to make a new identity

Can you tell the difference between a real face and one that was generated by artificial intelligence (AI)?

None of these are real people. This person does not exist.
Recently, Meta unmasked nearly 1,000 spy accounts on Facebook and Instagram posing as protesters, journalists, and young women. The tech giant warned that suspect profiles used AI-generated images and text to deceive users. Jimmy Patronis, Florida's Chief Financial Officer (CFO), echoed this concern, warning that social platforms like Facebook, Instagram, and X have become hotbeds of sophisticated fake business profiles—some of which even feature artificially generated human faces.
A now-removed Facebook profile created by generative AI.
Fake social media profiles like these can look incredibly real. But they’re actually part of coordinated disinformation campaigns. Once a phony profile starts amassing likes, follows, and retweets, it can be weaponized to commit identity fraud, spy on social media users, or spread misinformation on a massive scale.
The same thing is happening in financial services. Fraudsters are getting better at making these fake identities — also known as synthetic identities — look real. They are using them to perpetuate synthetic identity fraud (or synthetic identity theft), an activity the Federal Reserve has labeled “the fastest-growing type of financial crime in the U.S.”
We’re here to ask: where do synthetic identities come from? What makes them so dangerous? And what can be done to stop them?
A synthetic identity is born
No two synthetic identities share the same origin story. But before a synthetic ID is established, synthetic identity fraud often begins with identity theft. An identity thief might acquire a third party’s Personally Identifiable Information (PII) by stealing mail or by purchasing stolen social security numbers (SSNs) on the dark web.
Once a fraudster has acquired a stolen SSN, they assign it a new set of PII, including name, date of birth, and address. Using a combination of real and fake information, fraudsters can create new identities that appear convincing enough to bypass fraud detection systems. Fraudsters may extend a stolen SSN to create multiple synthetic identities for use across various fraud schemes.
It isn’t uncommon for fraudsters to form synthetic identities using bits of PII belonging to children, unhoused, or even deceased individuals. This is because PII sourced from individuals without a long-standing credit history can be valuable in synthetic identity formation.
Fraudsters understand that the more realistic each synthetic identity's digital “footprint” is, the more likely they are to bypass fraud mitigation measures. For this reason, once a fraudster has created a synthetic identity, they then have to mimic the internet behavior of a real person. A synthetic identity thief may try to legitimize their fake identity online by:
- Creating new email addresses
- Applying for new phone numbers
- Enrolling in rewards programs
- Setting up social media profiles
- Adding the identity to other public databases
With a victim’s SSN, a matching phony PII, and a solid digital footprint in place, the synthetic identity is ready for use. But where do fraudsters turn to commit synthetic identity fraud? And how do fraudsters use synthetic identities to exploit a financial institution’s (FI) vulnerabilities?
Fool me twice
A fraudster can’t exactly walk into a physical branch and apply for a loan using a deepfake. But online, one person can easily become dozens — if not hundreds — of fake individuals. Well-equipped with ways of making their synthetic identities look like they have financial histories — savvy fraudsters have fooled more than a few FIs.
Recommended for you: Ditch fraud at the doorstep: 3 tips for safer in-branch banking
Fraudsters will frequently start out by using their synthetic identity to apply for a credit product. This results in a rejection because the credit bureau will indicate to the FI that the applicant has no credit history. However, this very process also triggers the credit bureau to generate a new file belonging to the synthetic identity. The next time the fraudster applies for a product using this identity, the credit bureau will show a history — one that may be almost indistinguishable from that of a legitimate thin-file applicant.
The fraudster can then use this thin (but seemingly legitimate) new credit file to either:
- Apply for every credit product under the sun until they’re approved for one, then max out the line of credit and disappear.
Or:
- Apply for various financial products and establish a pattern of “good behavior” sufficient to qualify for a major credit product, then max out the line of credit and disappear.
There are variations in these basic schemes. A fraudster might somehow get the synthetic identity added as an authorized user on a legitimate account, for example, or establish a credit history using utility bills. However, in nearly all cases, the synthetic identity is used to obtain credit and later “bust out,” once they pass the credit limit, leaving the lending institution with delinquent accounts and no easy way to collect. This also damages the credit score of the real person whose personal data was stolen to fabricate the synthetic identity. Once someone’s credit report has been impacted by synthetic identity fraud, it can take years to rebuild, impacting their ability to work with lenders in the future.
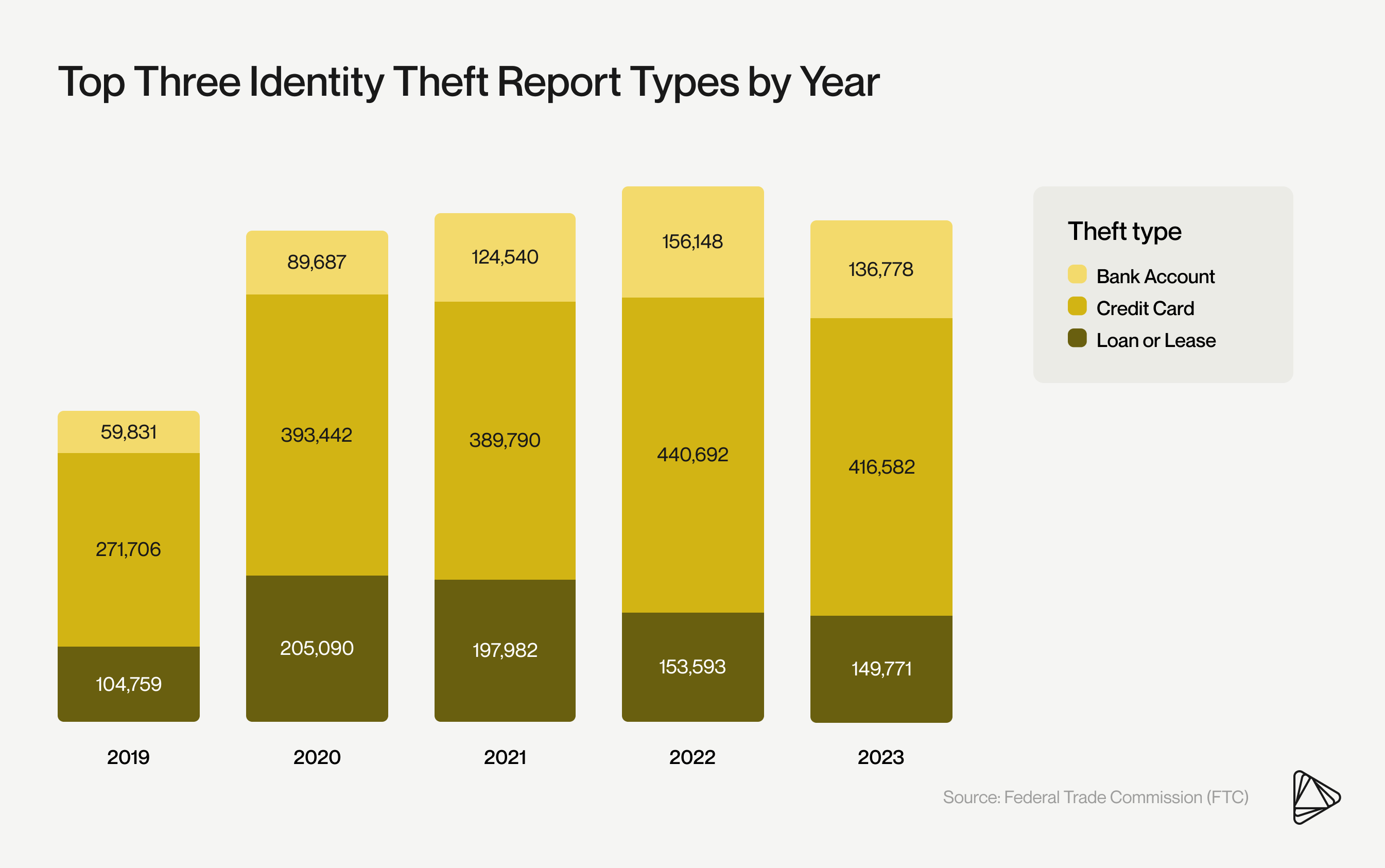
Credit cards remain the primary channel for identity theft, according to the Federal Trade Commission (FTC).
In 2023, the FTC received 416,582 reports of identity theft related to fraudulent credit card usage. Among all identity theft reports submitted to the FTC, 15% involved multiple forms of identity theft.
Cases of synthetic identity theft are likely underreported. In fact, Alloy’s 2024 State of Fraud Benchmark Report revealed that UK decision-makers at banks, credit unions, fintechs, and electronic money institutions (EMIs) are two times more likely than their US counterparts to list both synthetic fraud and identity theft as their most common type of fraud.
Part of the issue with synthetic fraud is that it is often mislabeled as first-party, friendly, chargeback, or bust-out fraud. And when a fraud type is mislabeled, it can be harder for financial organizations to fight back.
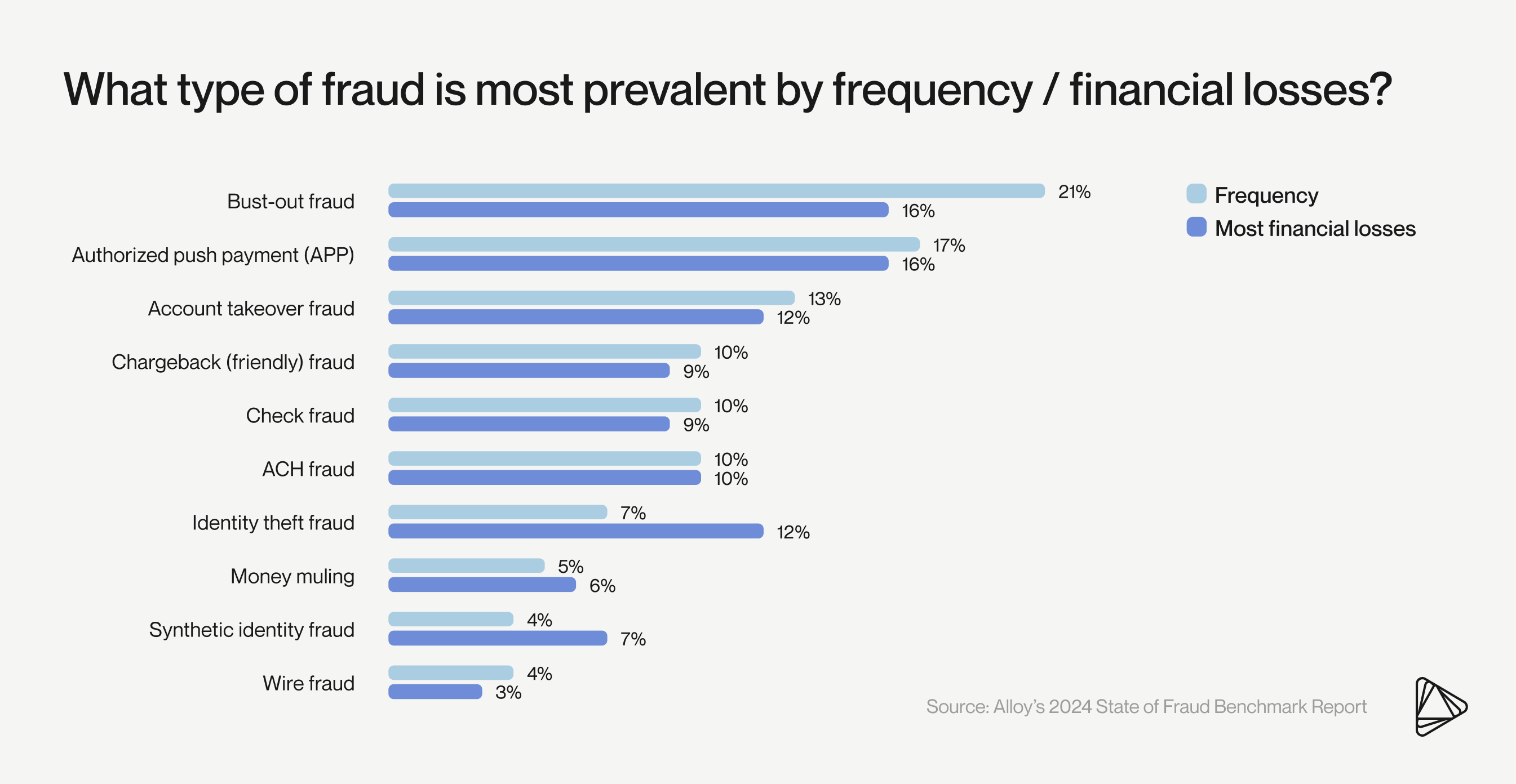
Fortunately, data helps make this threat visible. Between 2022 and 2023, applications with inconsistent PII increased 14% year-over-year (YOY), according to Alloy’s Benchmark Report. This is consistent with the prediction that fraudsters who benefitted from data breaches in 2020 would introduce new synthetic identities after 3-5 years spent “warehousing” them to build up a believable credit history.
Stopping synthetic identity fraud
AI may be improving, but the telltale signs of AI-generated faces remain the same: mismatched earrings, blurry backgrounds, or oddly symmetrical eye placement.

Mismatched earrings can give away an AI-generated face.
In fraud detection, teams can assess specific traits to manually identify a set of identities as synthetic. This approach to data only works if the identities are assessed together, not in isolation.
For example, if you see multiple applicants with shared PII attributes opening bank accounts or applying for the same product simultaneously, what are the chances they are legitimate? While it's possible that two individuals sharing the same last name and address could apply for the same product at the same time, it could also indicate that a fraud ring has generated several synthetic identities and is using them to apply for multiple lines of credit or open numerous bank accounts with your FI.
While combing through a stack of applications manually to find potential synthetics isn’t feasible, evaluating fraudulent activity using a synthetic-specific fraud model is. Fraud risk management solutions leveraging machine learning (ML) can tell when an SSN was generated, how many credit inquiries are associated with it, and whether the PII elements provided are actually a match.
Identity verification processes can also help prevent synthetic identity fraud. By using a combination of document verification, biometric authentication, and data cross-referencing, FIs can better ensure that their customers with seemingly good credit profiles aren’t matching a false identity to a real SSN. Advanced facial recognition systems can also use AI and ML models to detect signs of liveness and match the customer's face to their ID. This multi-layered approach to identity verification and authentication makes it harder for synthetic IDs to bypass fraud detection.
Alloy is your end-to-end Identity Risk Solution
Synthetic identity fraud is a growing problem. So, how do you know which customers are keeping it real and which ones are part of an elaborate scam?
Even for professional fraudsters, creating synthetic identities is hard work. Fraud rings go to extraordinary lengths to make synthetic identities look real because the eventual payday can be worth it: fraudsters can make up to six-figure sums per synthetic ID.
Driving fraudsters out of business is hard work, especially when they’re using Frankenstein identities. It’s up to FIs to leverage synthetic fraud modules and behavioral analytics to automatically spot synthetic identities at onboarding and throughout the customer lifecycle. Integrating ML models with specifications to meet your risk tolerance will help combat the current threat.
Alloy’s Identity Risk Solution is a holistic platform for detecting and preventing synthetic identity fraud. By leveraging advanced analytics, machine learning, and a vast network of data sources, Alloy helps you verify the authenticity of your customers' identities at every stage of the customer journey. Our ongoing identity monitoring begins at onboarding, helping to increase your FI’s number of good approvals while reducing manual reviews. The result? Less fraud within your banking or embedded finance ecosystem and a seamless user experience made to fit your risk tolerance.





