Share
What is ambient fraud?
Feb 27, 2023
The most common type of fraud is one you might not have heard of yet. Here’s how to identify and combat ambient fraud.
Fraud attacks can seemingly come out of the blue. One day, you’re happily onboarding new customers—the next, you see an unusual (or downright bizarre) spike in applications at the top of the funnel.
But before the fraud attack, you’ll almost certainly experience a different, equally dangerous type of fraud: ambient fraud.
The threat of ambient fraud
Ambient fraud happens every day. It consists of one-off, low-profile fraud attempts that may be so commonplace as to fly under your radar altogether. Most financial institutions (FIs) see a steady inflow of this type of fraud, and many argue that this type of fraud is “just a cost of doing business,” however, as soon as the vulnerability gets exposed, fraud losses can quickly quadruple.
Ambient fraud is dangerous because it’s how fraudsters uncover vulnerabilities in your fraud defenses. Once a vulnerability is found, the next step may be a fraud attack.
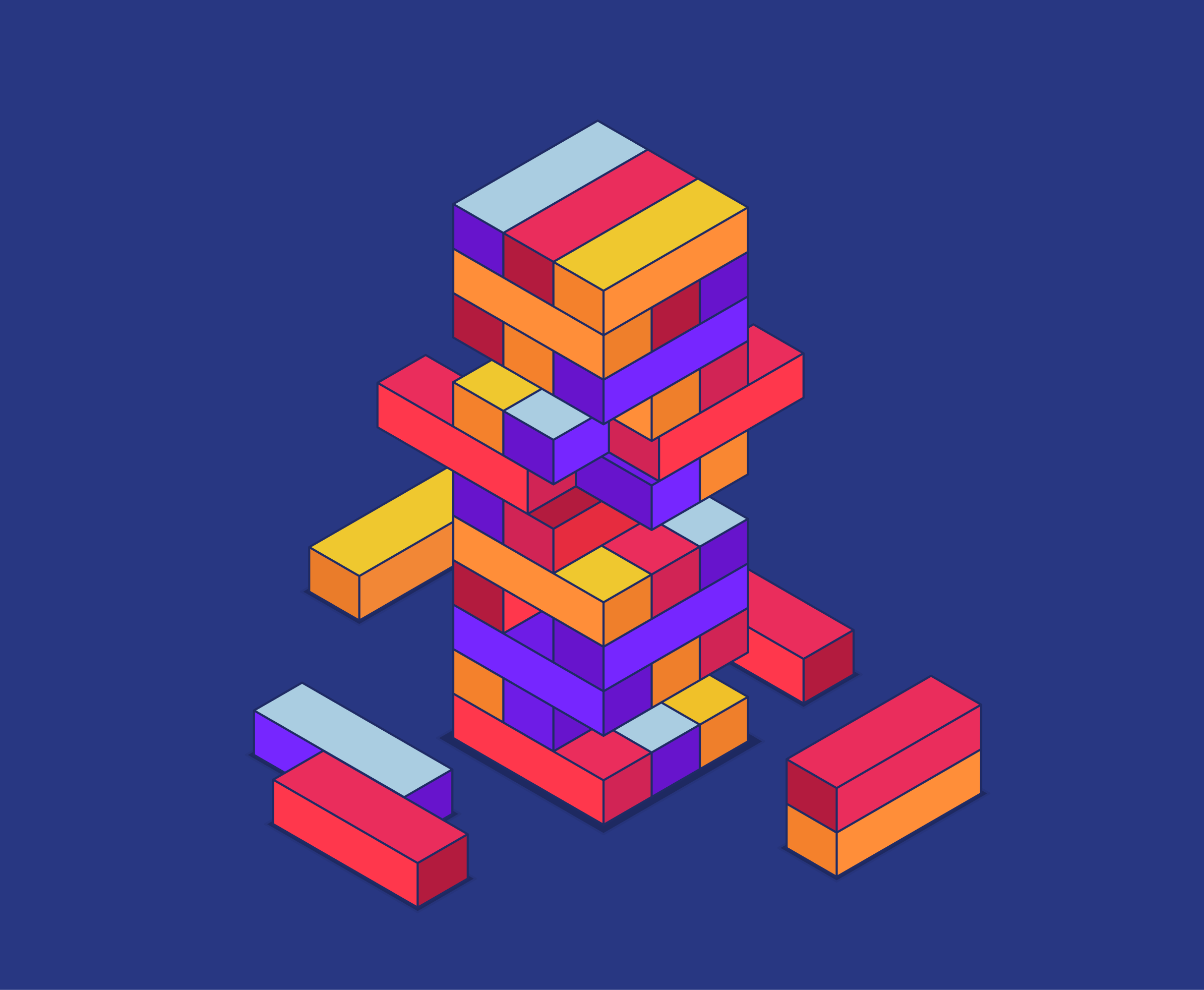
Think of Jenga. In Jenga, players take turns removing wooden blocks from a stacked tower until it eventually collapses. Rather than going for the first block they see, smart players prod, nudge, and adjust blocks until they find one that will be easy to remove.
Fraudsters take a similar approach. Fraud pros constantly test your fraud controls “Jenga tower” for easy blocks to pull. This testing activity (along with smaller-scale fraud from amateurs and first-party fraudsters) is ambient fraud. Many banks and fintech companies see ambient fraud on a daily basis, but brush it off due to its small scale or because it was easily caught. But with every test, fraudsters learn more about you, and these scouting missions can turn into a full-scale attack causing your tower to fall.
Ambient fraud vs. fraud attacks
Ambient fraud offers fraudsters the chance to collect intel that may be useful for attacking other financial institutions (FIs). In fact, fraudsters often form “fraud farms” where they pay people around the world to cycle through different financial institutions and see what controls can be breached.
Another major challenge facing FIs is that it’s not always easy to distinguish between ambient fraud and a fraud attack. You can mistake ambient fraud for a fraud attack, or vice versa, because any instance of fraud could precede an imminent larger-scale attack.
According to Alloy’s fraud response guide, there are two types of fraud attacks. Here’s how to identify which is which:
Fraud ring attacks are characterized by a number of accounts with shared features such as PII or funding sources. These attacks tend to involve relatively large losses per account.
High-velocity attacks are characterized by a surge in application volume. These attacks are more obvious but can quickly overwhelm the financial institution. A lot of FIs choose to turn off auto-approval temporarily and route everything to manual review, which then puts stress on the reviewers and resources.
What can you do about ambient fraud?
Get agile. The most important factor to consider in terms of fraud prevention is that the landscape is always changing: fraud methods change, new technologies, and payment methods mutate, new regulations come up. FIs need a fraud tech stack that can easily and quickly adapt to changes in the ecosystem to future-proof fraud controls against tomorrow’s fraudsters. Alloy is an orchestration platform known for speed and ease of changing or adding different data vendors in your onboarding process.
Implement industry best practices. Approaching fraud and identity verification from multiple angles is key to mitigating risk. Use multiple data sources to capture actionable signals about the applicant, including services like behavioral analytics, velocity checks, machine-learning-based fraud scoring, and step-up authentication. Alloy provides guidance on how best to structure these data services in your workflows to reduce your susceptibility to a fraud attack and better equip you to manage an attack if it happens. The correct sequencing of the data services can also mean cost savings.
Set up robust alerting mechanisms if something goes wrong. The faster you learn that a fraudster has found a vulnerability in your controls, the faster you can correct the issue. Alloy has partnered with NeuroID, which offers a free alerting tool called ID Crowd Alert. Neuro-ID monitors applicants’ familiarity with the data they provide in digital applications, and then visualizes and notifies clients when behavior associated with fraud rings, automated activity, and other risky behavior is observed.
Analyze and learn from your data. Analyzing the patterns among accounts closed for fraudulent reasons is a great learning opportunity for FIs to make their workflows more robust.
It’s also natural, in the aftermath of a fraud attack, to feel sensitive toward fraud. It’s natural to want tighter controls in place so that it doesn’t happen again. Nevertheless, after a fraud attack, financial institutions also face pressure to reopen the funnel to meet new customer conversion targets. With careful monitoring, consistent analysis of final outcomes data, and the flexibility to change your workflows at the speed of fraud through Alloy, your institution should be in better shape to fight fraud.